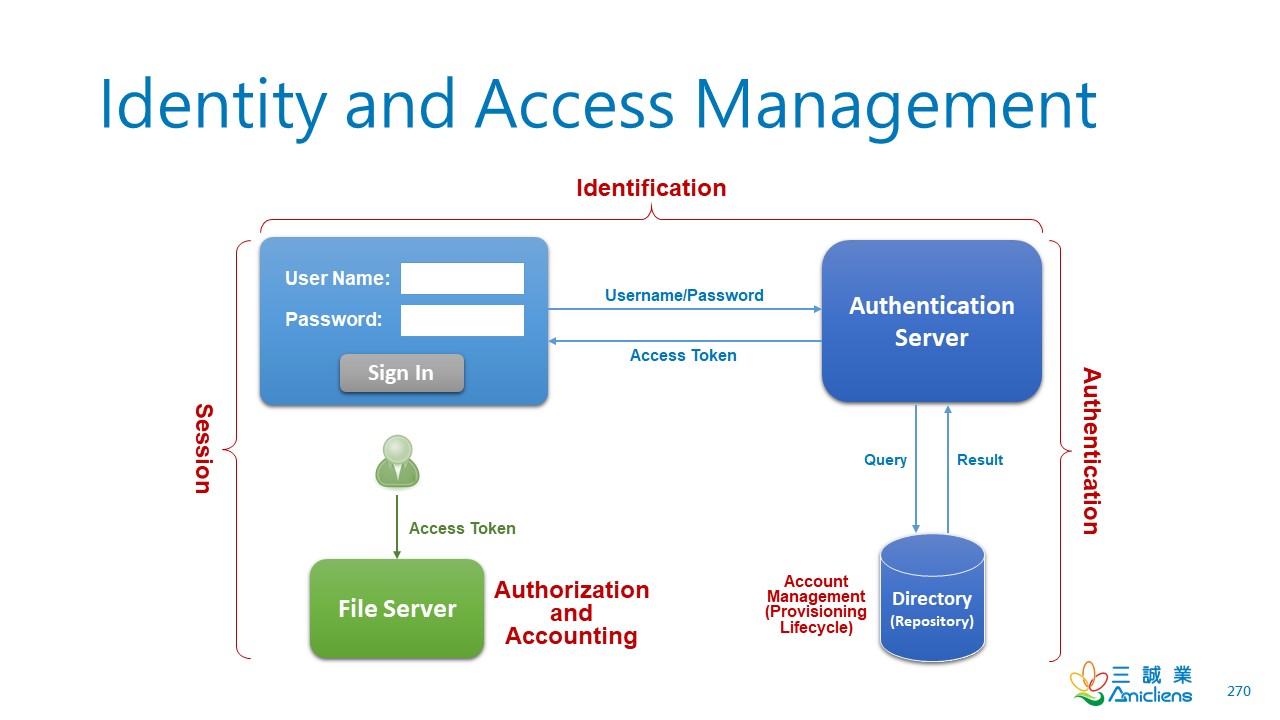
Identity and Access Management by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
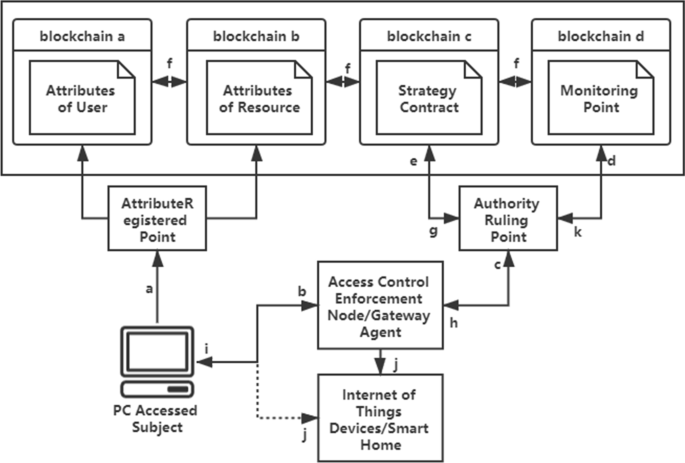
An access control model for the Internet of Things based on zero-knowledge token and blockchain | EURASIP Journal on Wireless Communications and Networking | Full Text
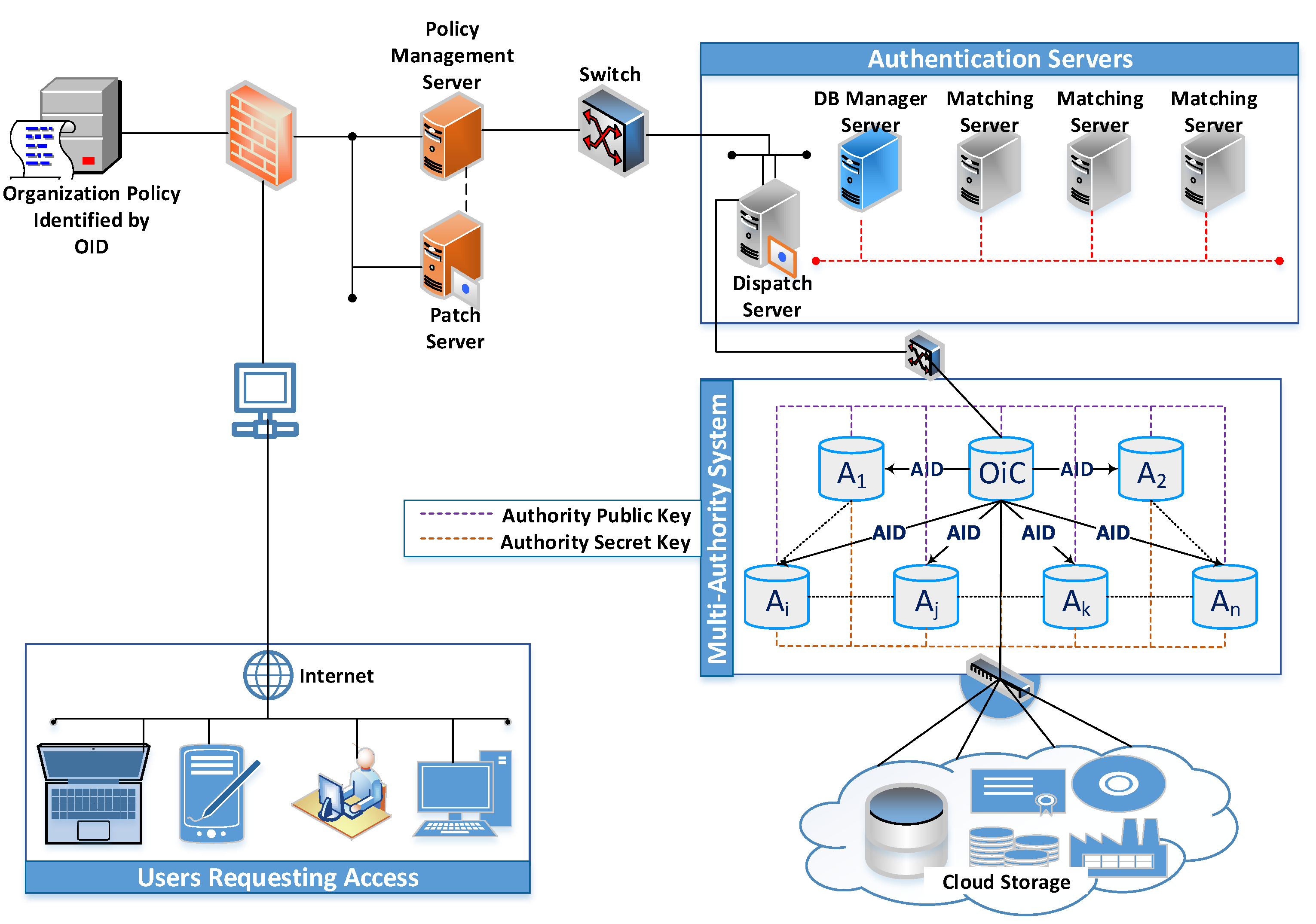
Applied Sciences | Free Full-Text | Token-Revocation Access Control to Cloud-Hosted Energy Optimization Utility for Environmental Sustainability

Smart contract token-based privacy-preserving access control system for industrial Internet of Things - ScienceDirect
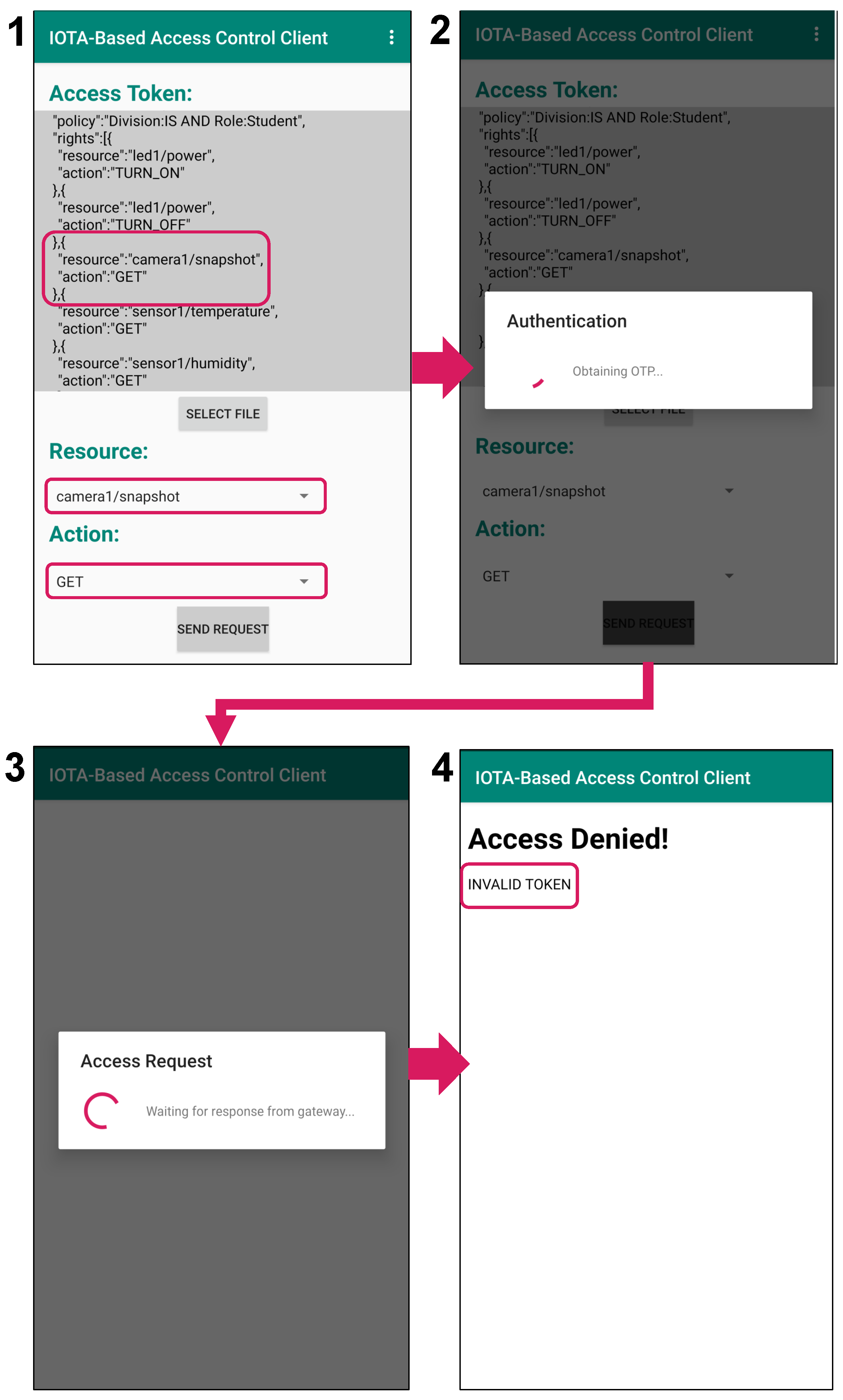


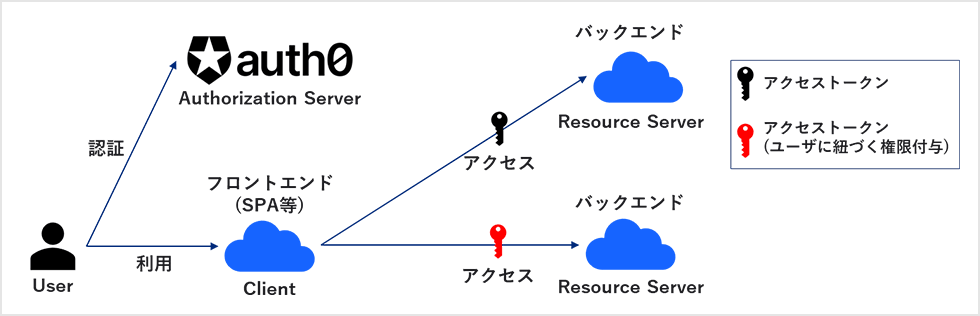



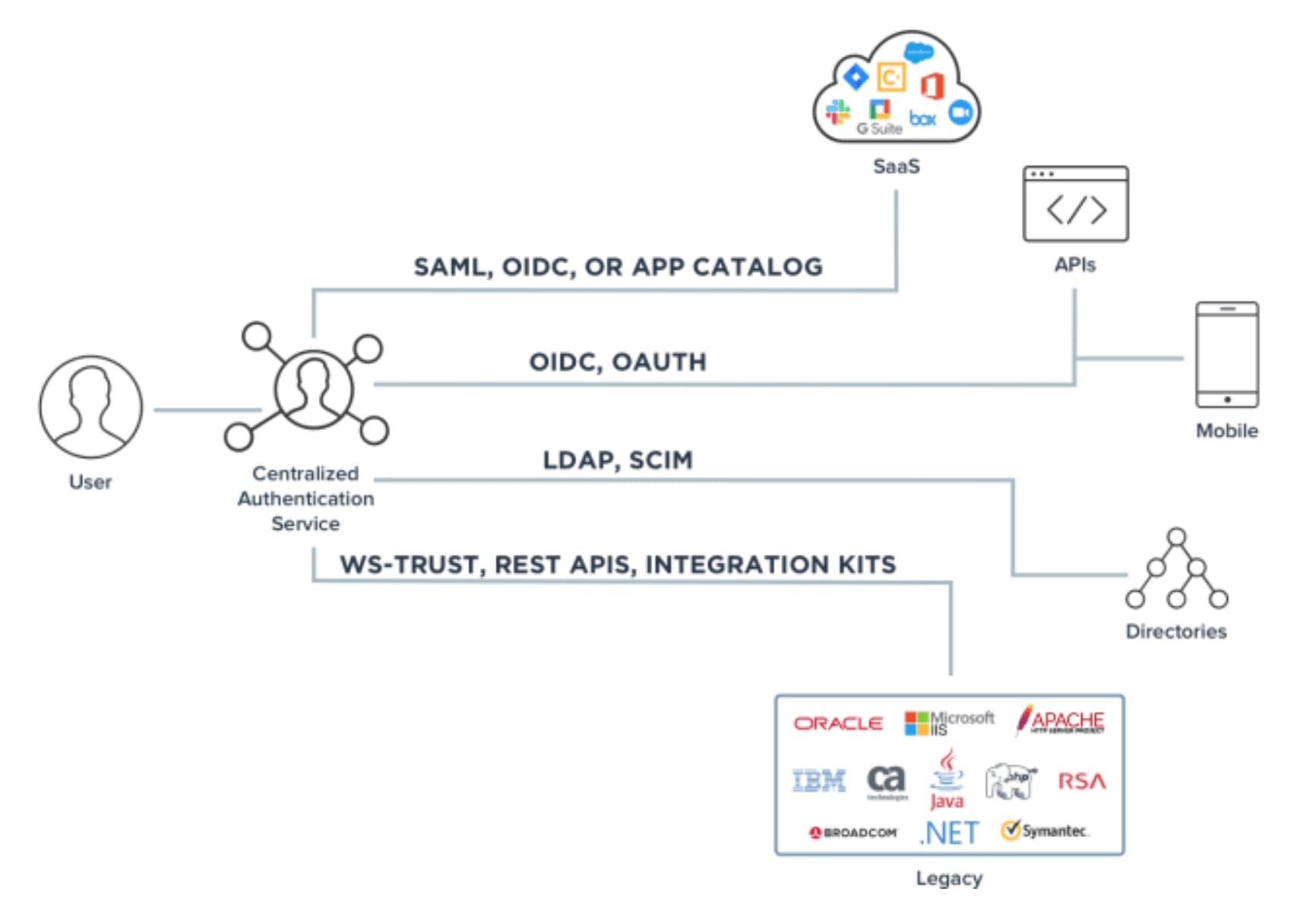
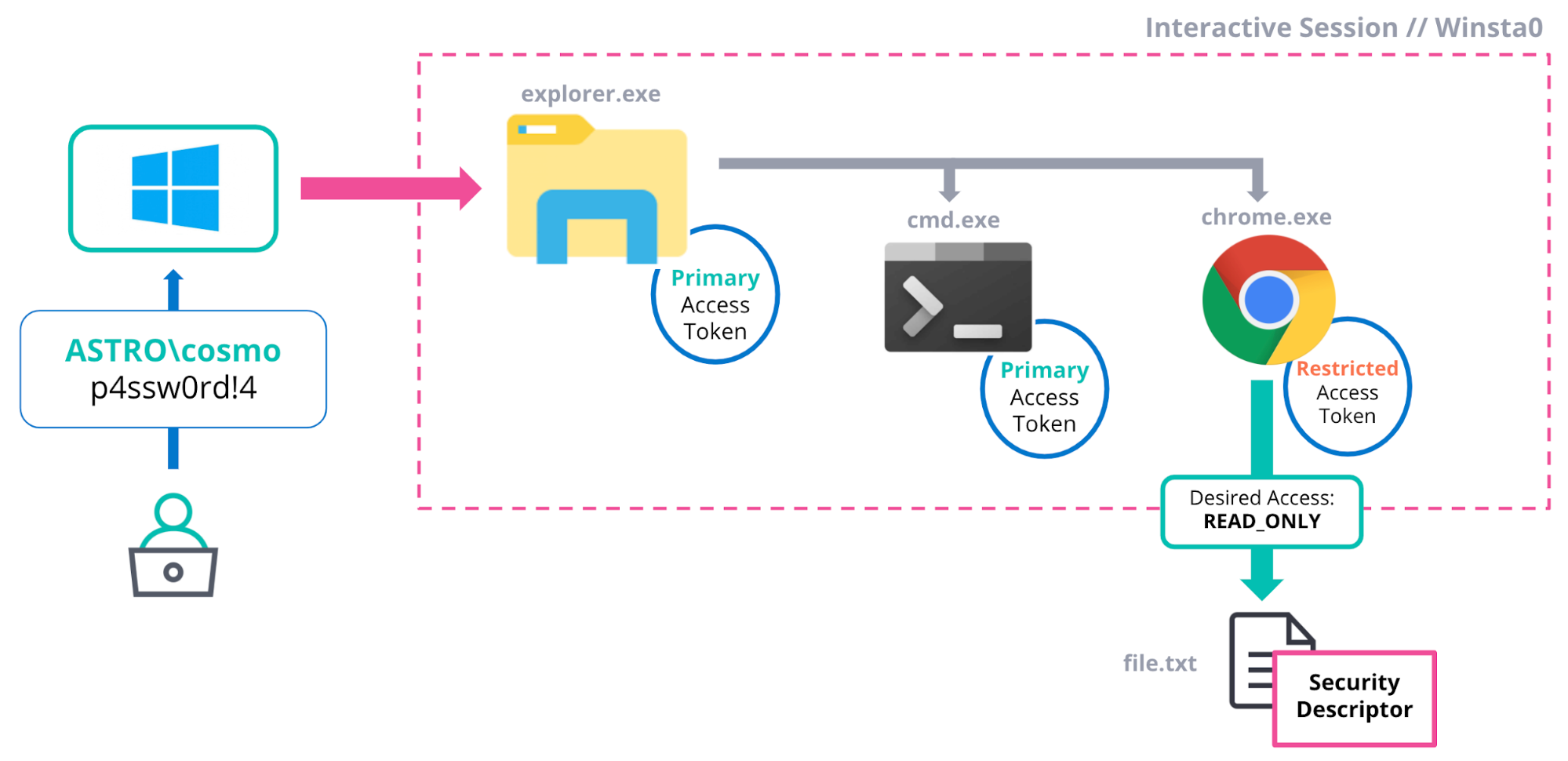
![PDF] Token-Based Access Control | Semantic Scholar PDF] Token-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b32999942637ff5dd4944c4edaa685762a3898ab/3-Figure1-1.png)