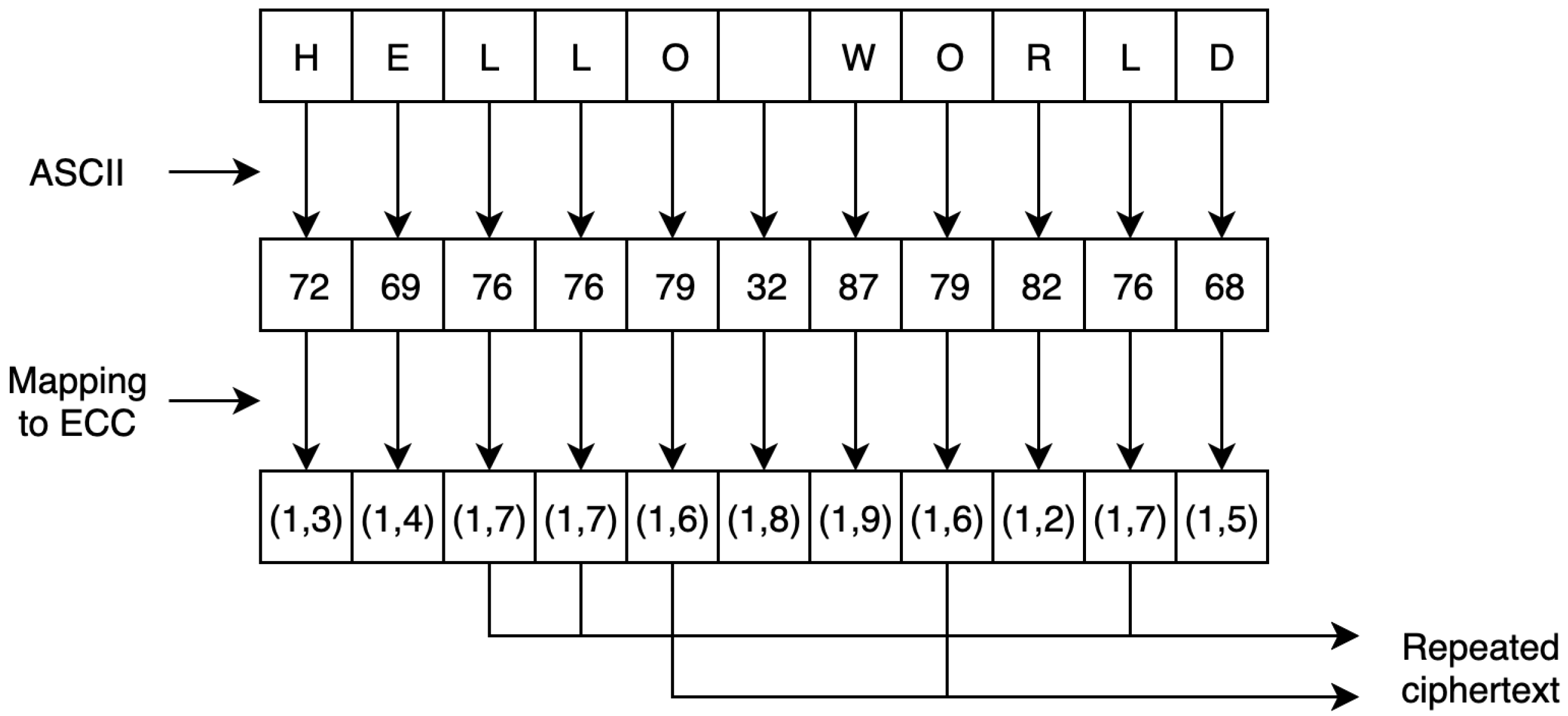
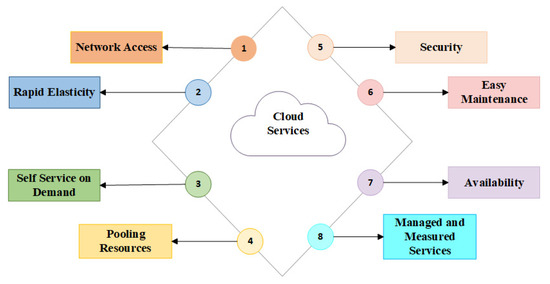
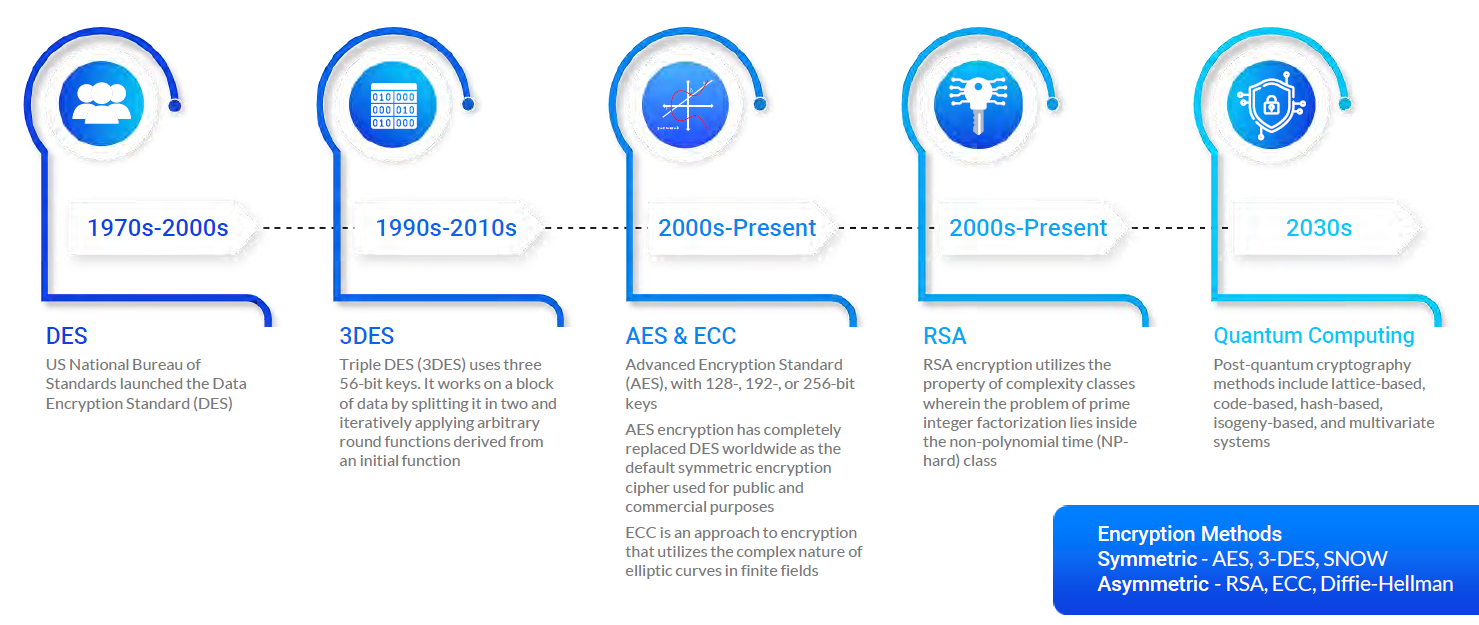
Sensors | Free Full-Text | A Secure and Efficient ECC-Based Scheme for Edge Computing and Internet of Things

OFFTEK 32GB Ersatz Arbeitsspeicher RAM Memory für Penguin Computing Rackmount Relion 2940 Großrechner/Server-Speicher: Amazon.de: Computer & Zubehör

Advances in Unconventional Computing: Volume 1: Theory (Emergence, Complexity and Computation, 22, Band 22) : Adamatzky, Andrew: Amazon.de: Bücher

SEBAP: A secure and efficient biometric‐assisted authentication protocol using ECC for vehicular cloud computing - Kumar - 2021 - International Journal of Communication Systems - Wiley Online Library

Comparison of computation time for key generation between ECC and NTRU | Download Scientific Diagram

2: Implementation of ECC data in Cloud computing (simulation of The... | Download Scientific Diagram

Team Group Releases DDR5 VLP ECC UDIMM Industrial Memory for NetCom and High Computing Power Applications | TechPowerUp