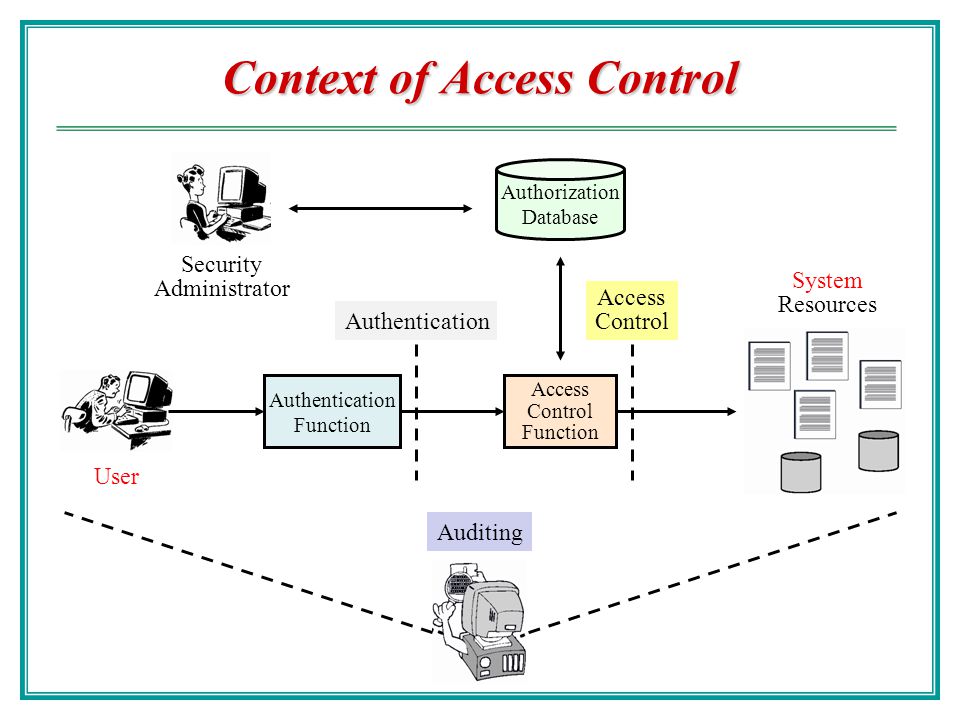
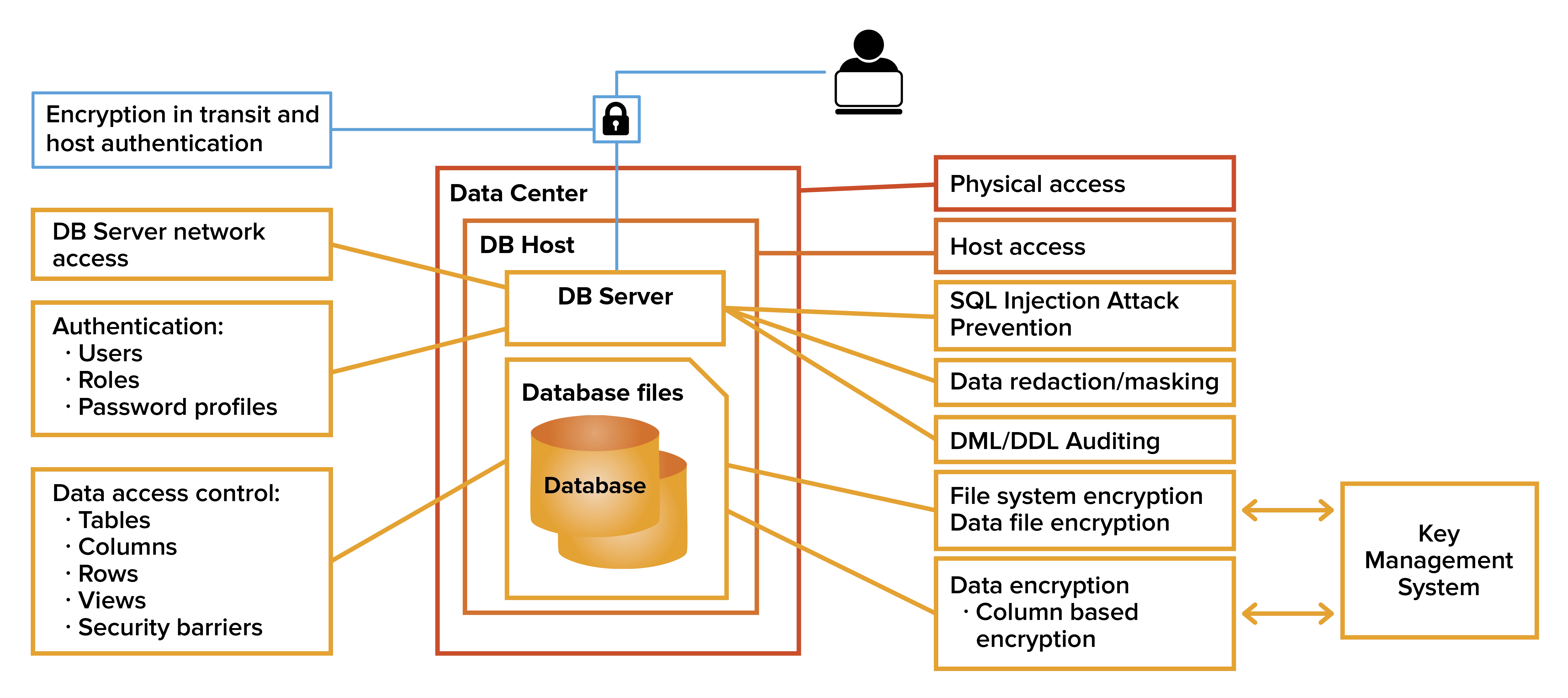
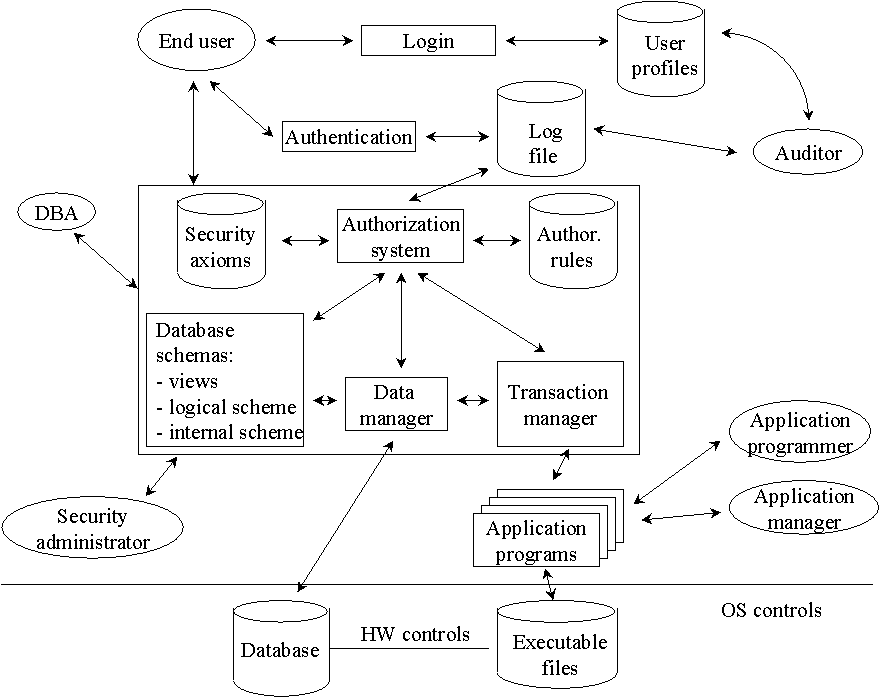
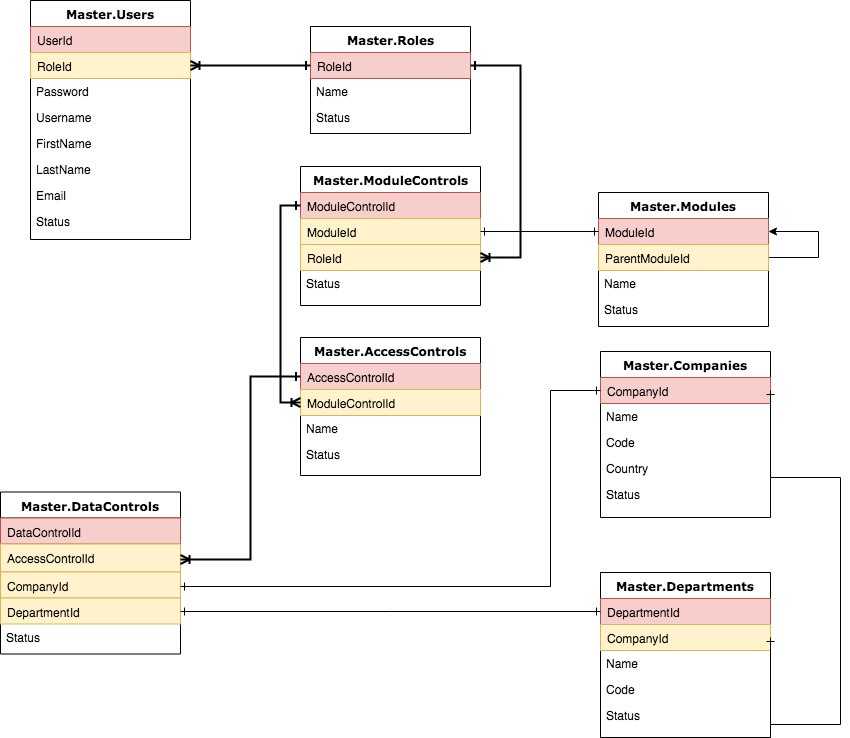
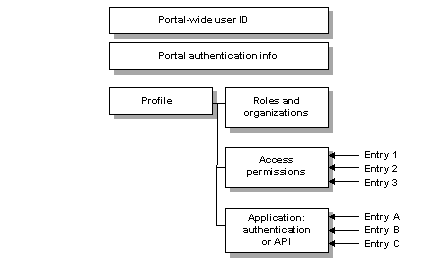
Database Security and Authorization Introduction to DB Security Access Controls Database Security and the DBA Discretionary Access Control The privileges. - ppt download
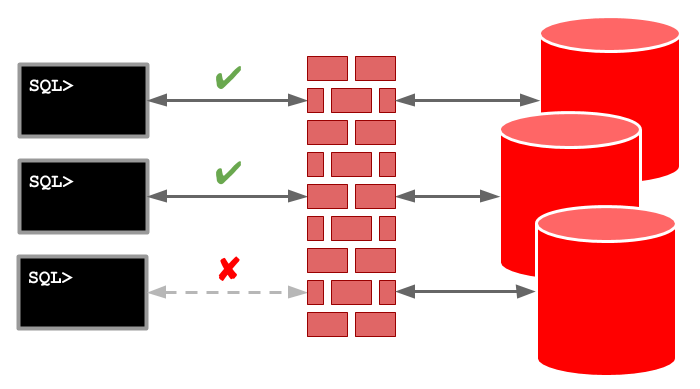
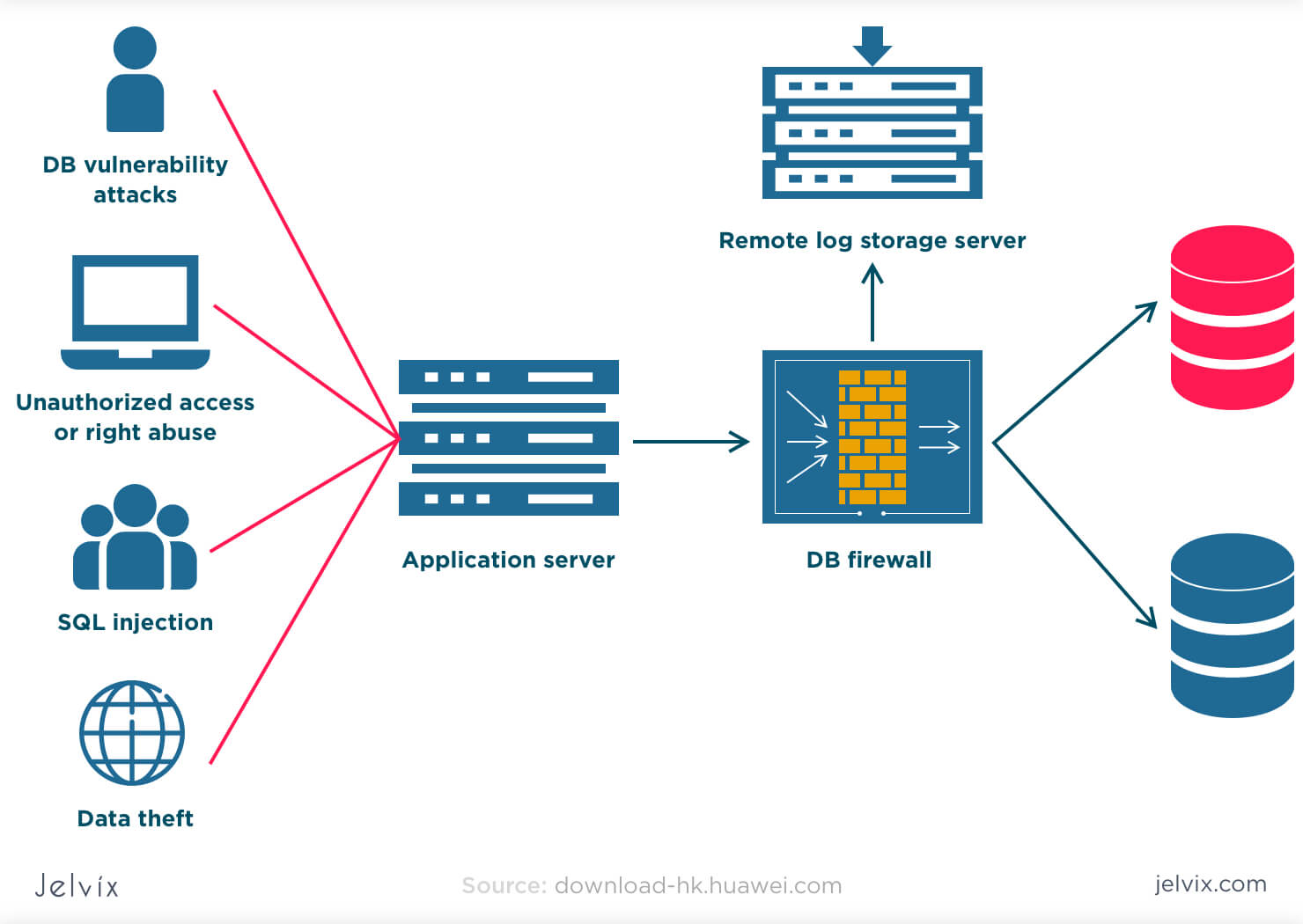
ORACLE-BASE - Service-Level Access Control Lists (ACLs) - Database Service Firewall in Oracle Database 12c Release 2 (12.2)


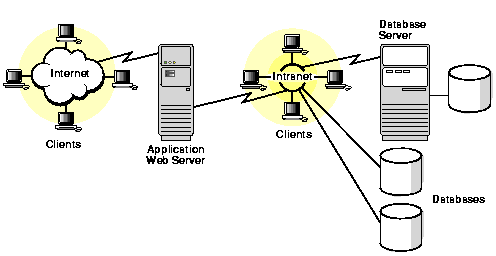



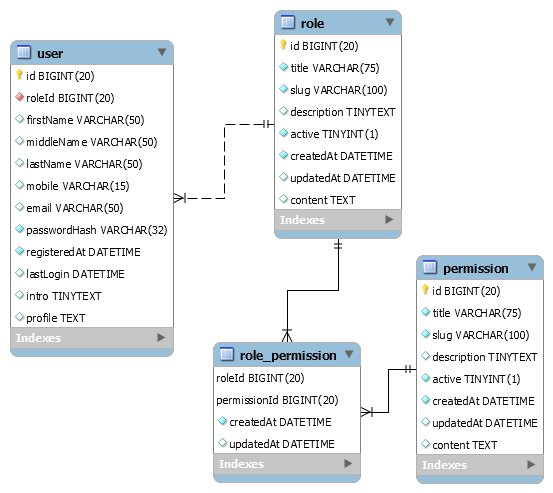
![PDF] Don't Even Ask: Database Access Control through Query Control | Semantic Scholar PDF] Don't Even Ask: Database Access Control through Query Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fbbb736712ba0272d406143d7a25835c177861e/2-Figure1-1.png)
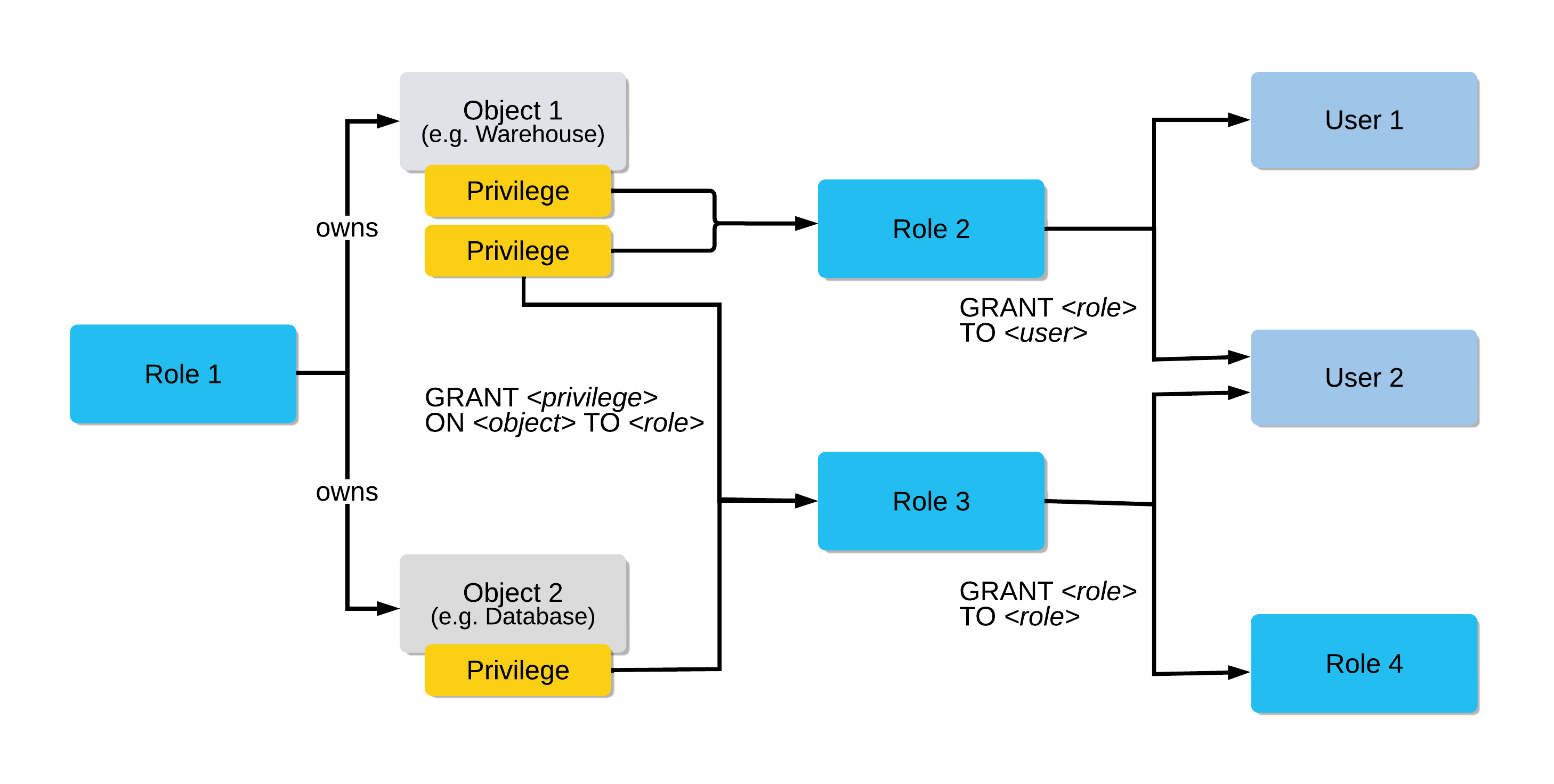
![PDF] Database Access Control Policies | Semantic Scholar PDF] Database Access Control Policies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bfd4c8c86b964e3843b853d311181a12267c5633/3-Figure3-1.png)